Use Case
A domain joined laptop can access a web server (Like Citrix Web Interface server?) which allows Kerberos Authentication ONLY.
But when the same Laptop goes remote and access the web page through a reverse proxy or ADC(like Netscaler) it is denied access( or authentication falls back to NTLM and user gets a login prompt).
The Login prompt in undesirable.
Solution -
Use user certificates to make authentication process transparent to the client and use AAA virtual servers to single sign on to the Web application using "Constrained Kerberos Delegation".
The client machine has a user certificate installed from corporate CA
Network Diagram
Detailed Configuration
Domain Configuration -
Create a domain account - sun\kdcsvc.
and run the following command to set service principal name and enable delegation for that account
setspn -A host/iislb.sun.ad SUN\KDCSV
Points to note here are -
1> "iislb.sun.ad" is the FQDN which I will use to access this web server from outside the corporate LAN.
2> This FQDN should get resolved to a public IP hosted on the Netscaler and used by the Content Switching(or Unified Gateway!!) or Load Balancing Virtual Server.
3> This should be the subject name of your SSL certifcate.
4> I have a wild card SSL certificate - this was helpful as I am not quite sure why a non-addressable AAA VS server needs an SSL certificate and if it does what should be its subject name.
5> During troubleshooting of my setup I figured out that the Netscaler was sending the http get requests to http/client01.sun.ad. where client01.sun.ad is the host name of my IIS webserver( yeah!! I did not think it through, but when you have 8 GB RAM on your hypervisor you tend to do a lot of use and reuse and abuse!!).
So I added SPN to the delegation account -
setspn -A http/client01.sun.ad SUN\KDCSVC
Now, I am not sure if it helped or not. I think I will remove this SPN and test again.
After you run the above command to enable delegation, you will see a new tab in the user properties window on your AD -
Select the highlighted options exactly as above. Any other combination does not work.
Click on add, search for your IIS servers in AD, and select HTTP service to configure delegation for the selected services.
Note that Constrained Delegation does not support Services hosted in other Domains even if there is a trust relationship between those Domains
Generate Keytab file
Although Netscaler can help you generate a script, to run on your domain controller, to generate a keytab file but I found that GUI - not very intuitive.
The command to generate a keytab file for the user "sun\kdcsvc" for the SPN "host/iislb.sun.ad" is -
ktpass /princ host/iislb.sun.ad@SUN.AD /ptype KRB5_NT_PRINCIPAL /mapuser sun\kdcsvc /pass freebsd -out C:\kdcsvc.keytab
SCP this keytab to the /nsconfig/krb directory on Netscaler. Up till build 10.5 - if you have this file in any other directory, Netscaler will not read it.
Web-server configuration
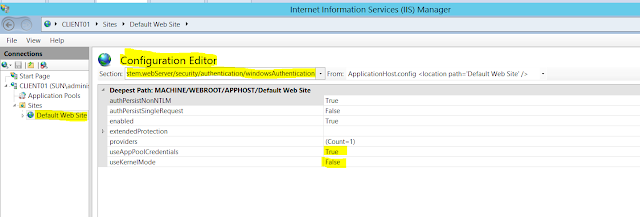
I followed this link to configure my IIS 7 default website to configure "Negotiate" authentication provider and allow "sun\kdcsvc" to do Kerberos delegation.
A point to note here - In IIS 6 there is no provider type as - "Negotiate:Kerberos", So configure "Negotiate" - which means that the web server will fall back to NTLM if Kerberos is not successfully negotiated as the authentication mechanism.
Now the Netscaler Configuration -
Certificate based Authentication Policy
AAA Virtual Server
Load Balancing Server-
Refer the following screen shot to
1> Add a server under Configuration>>Traffic Management>> Load Balacing>> Servers
2> Add services under Configuration>>Traffic Management>> Load Balancing>>Services
3> Add a load balancing virtual Server.
Testing -
1> Issue and install a user certificate from the same CA which issued the web server certificate. The certificate should be installed on the test laptop. Point to be noted here a user certificate is different from a web server certificate - its "USAGE" is different.
2> Make a host file entry to your test laptop
"192.168.1.114 iislb.sun.ad"
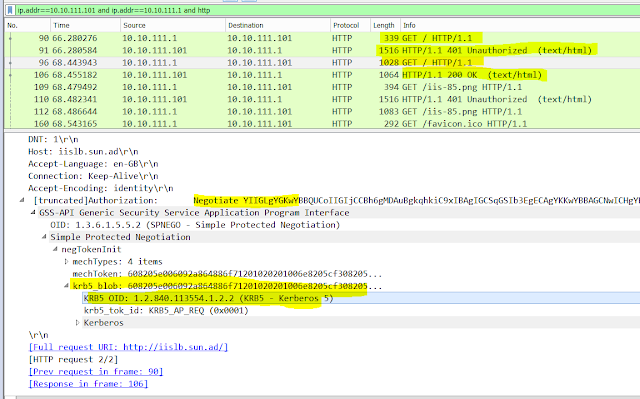
3> Install Wireshark on the web server (client01.sun.ad) and apply the following filter to catch relevant traffic -
ip.addr==10.10.111.1 and ip.addr==10.10.111.101 and http.
for the purpose of this test, I changed the monitor of my load balancing service (on Netscaler) to ping from default.
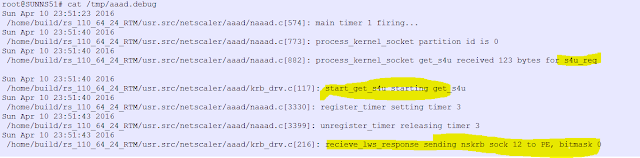
4> Go to shell on the Netscaler and execute
cat /tmp/nskrb.debug
5> Open browser on your test laptop and try to browse https://iislb.sun.ad. You should get a prompt to select certificate to authenticate. After you select the certificate you should see the home page your web application.
Troubleshooting/issue faced -
1> Use NSKRB commands to get the requested tickets. This will help to narrow down the area of concern -
2> Browse to /var/krb directory on the Netscaler. After a succesful kerberos authentication I see the following files in this folder -
3>
4> I did a new setup from scratch and did not add the SPN mentioned in step "5" of the "Domain Configuration" above. My Kerneros authentication failed with IIS server rejecting the Kerberos Ticket with KRB5KRB_ERR_GENERIC.
Added the SPN again and It started worked again!
I think some setting on the NeScaler should allow the "Server Name" in Kerberos String to set to my Load Balancer URL. I will explore more and add here.
A domain joined laptop can access a web server (Like Citrix Web Interface server?) which allows Kerberos Authentication ONLY.
But when the same Laptop goes remote and access the web page through a reverse proxy or ADC(like Netscaler) it is denied access( or authentication falls back to NTLM and user gets a login prompt).
The Login prompt in undesirable.
Solution -
Use user certificates to make authentication process transparent to the client and use AAA virtual servers to single sign on to the Web application using "Constrained Kerberos Delegation".
The client machine has a user certificate installed from corporate CA
Network Diagram
Detailed Configuration
Domain Configuration -
Create a domain account - sun\kdcsvc.
and run the following command to set service principal name and enable delegation for that account
setspn -A host/iislb.sun.ad SUN\KDCSV
Points to note here are -
1> "iislb.sun.ad" is the FQDN which I will use to access this web server from outside the corporate LAN.
2> This FQDN should get resolved to a public IP hosted on the Netscaler and used by the Content Switching(or Unified Gateway!!) or Load Balancing Virtual Server.
3> This should be the subject name of your SSL certifcate.
4> I have a wild card SSL certificate - this was helpful as I am not quite sure why a non-addressable AAA VS server needs an SSL certificate and if it does what should be its subject name.
5> During troubleshooting of my setup I figured out that the Netscaler was sending the http get requests to http/client01.sun.ad. where client01.sun.ad is the host name of my IIS webserver( yeah!! I did not think it through, but when you have 8 GB RAM on your hypervisor you tend to do a lot of use and reuse and abuse!!).
So I added SPN to the delegation account -
setspn -A http/client01.sun.ad SUN\KDCSVC
Now, I am not sure if it helped or not. I think I will remove this SPN and test again.
After you run the above command to enable delegation, you will see a new tab in the user properties window on your AD -
Select the highlighted options exactly as above. Any other combination does not work.
Click on add, search for your IIS servers in AD, and select HTTP service to configure delegation for the selected services.
Note that Constrained Delegation does not support Services hosted in other Domains even if there is a trust relationship between those Domains
Generate Keytab file
Although Netscaler can help you generate a script, to run on your domain controller, to generate a keytab file but I found that GUI - not very intuitive.
The command to generate a keytab file for the user "sun\kdcsvc" for the SPN "host/iislb.sun.ad" is -
ktpass /princ host/iislb.sun.ad@SUN.AD /ptype KRB5_NT_PRINCIPAL /mapuser sun\kdcsvc /pass freebsd -out C:\kdcsvc.keytab
SCP this keytab to the /nsconfig/krb directory on Netscaler. Up till build 10.5 - if you have this file in any other directory, Netscaler will not read it.
Web-server configuration
I followed this link to configure my IIS 7 default website to configure "Negotiate" authentication provider and allow "sun\kdcsvc" to do Kerberos delegation.
A point to note here - In IIS 6 there is no provider type as - "Negotiate:Kerberos", So configure "Negotiate" - which means that the web server will fall back to NTLM if Kerberos is not successfully negotiated as the authentication mechanism.
Certificate based Authentication Policy
AAA Virtual Server
Load Balancing Server-
Refer the following screen shot to
1> Add a server under Configuration>>Traffic Management>> Load Balacing>> Servers
2> Add services under Configuration>>Traffic Management>> Load Balancing>>Services
3> Add a load balancing virtual Server.
Testing -
1> Issue and install a user certificate from the same CA which issued the web server certificate. The certificate should be installed on the test laptop. Point to be noted here a user certificate is different from a web server certificate - its "USAGE" is different.
Install a user certificate on the test machine..
2> Make a host file entry to your test laptop
"192.168.1.114 iislb.sun.ad"
3> Install Wireshark on the web server (client01.sun.ad) and apply the following filter to catch relevant traffic -
ip.addr==10.10.111.1 and ip.addr==10.10.111.101 and http.
for the purpose of this test, I changed the monitor of my load balancing service (on Netscaler) to ping from default.

4> Go to shell on the Netscaler and execute
cat /tmp/nskrb.debug
5> Open browser on your test laptop and try to browse https://iislb.sun.ad. You should get a prompt to select certificate to authenticate. After you select the certificate you should see the home page your web application.
Troubleshooting/issue faced -
1> Use NSKRB commands to get the requested tickets. This will help to narrow down the area of concern -
2> Browse to /var/krb directory on the Netscaler. After a succesful kerberos authentication I see the following files in this folder -
3>
4> I did a new setup from scratch and did not add the SPN mentioned in step "5" of the "Domain Configuration" above. My Kerneros authentication failed with IIS server rejecting the Kerberos Ticket with KRB5KRB_ERR_GENERIC.
Added the SPN again and It started worked again!
I think some setting on the NeScaler should allow the "Server Name" in Kerberos String to set to my Load Balancer URL. I will explore more and add here.